November 19, 2015—The Nmap Project is pleased to announce the immediate, free availability of the Nmap Security Scanner version 7.00 from https://nmap.org/. It is the product of three and a half years of work, nearly 3200 code commits, and more than a dozen point releases since the big Nmap 6 release in May 2012. Nmap turned 18 years old in September this year and celebrates its birthday with 171 new NSE scripts, expanded IPv6 support, world-class SSL/TLS analysis, and more user-requested features than ever. We recommend that all current users upgrade.
Contents:
Nmap was named “Security Product of the Year” by Linux Journal, Info World, LinuxQuestions.Org, and Codetalker Digest. It was even featured in nineteen movies and TV series, including The Matrix Reloaded, The Bourne Ultimatum. Girl with the Dragon Tattoo, Dredd, Elysium, and Die Hard 4. Nmap was released to the public in 1997 and has earned the trust of millions of users.
As free software, we don't have any sort of advertising budget. So please spread the word that Nmap 7 is now available!
Reasonably detailed (or with many comments) English articles:
Permission is granted for journalists (or anyone writing about this Nmap release) to use any of the text or screen shots on this page. For quotes, you can email Fyodor atfyodor@nmap.org. Leave your phone number if you want a callback.
Zenmap is our cross-platform (Linux, Windows, Mac OS X, etc.) Nmap GUI and results viewer. It aims to provide advanced features for experienced Nmap users while also making Nmap easier for beginners to use. Frequently used scans can be saved as profiles to make them easy to run repeatedly. A command creator allows interactive creation of Nmap command lines. Scan results can be saved and viewed later, or even compared with one another to see how they differ. Our network topology viewer allows for interactive exploration of a network scanned with Nmap. Zenmap is now a mature tool, but it still got several enhancements since 6.00:
We are excited and proud to announce that Ncat has been adopted by the Red Hat/Fedora family of distributions as the default package to provide the "netcat" and "nc" commands! This cooperation has resulted in a lot of squashed bugs and enhanced compatibility with Netcat's options.
Some of the most exciting changes in Ncat 7 are:
In addition to more than 1400 new fingerprints, we made several important performance improvements and bug fixes to the system. Most notably, if version detection determines a port to be "tcpwrapped," OS detection will prefer to use a different port for probing, since there's a good chance this is the result of a firewall interfering with TCP connections on that port.
Additionally, Nmap 7 has 23 more service probes to pull information from remote services and more than double the number of softmatch lines (103), which help short-circuit the probing process to send the most-likely probes for the detected service.
For the latest Insecure.Org and Nmap announcements, join the 117,175-member Nmap-hackers announcement list. Traffic rarely exceeds one message per month. Subscribe here orread the archives at SecLists.Org. To participate in Nmap development, join the (high traffic) nmap-dev list. You can also follow us on Twitter, Facebook, or Google+.
We would also like to thank the thousands of people who have submitted OS and service/version fingerprints, as well as everyone who has found and reported bugs or suggested features.
Special thanks go to Google, who has sponsored 73 students (total over the last 11 years) to spend a summer working on Nmap as part of Google's Summer of Code program. This summer, we had a team of five amazing students who contributed mightily to make Nmap even more powerful. We encourage you to read this year's project summary to learn more.
Contents:
- About Nmap
- Top 7 Improvements in Nmap 7
- Press
- Screen Shots
- Detailed Improvements
- Moving Forward (Future Plans)
- Acknowledgments
- Download and updates
About Nmap
Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for network inventory, managing service upgrade schedules, monitoring host or service uptime, and many other tasks. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).Nmap was named “Security Product of the Year” by Linux Journal, Info World, LinuxQuestions.Org, and Codetalker Digest. It was even featured in nineteen movies and TV series, including The Matrix Reloaded, The Bourne Ultimatum. Girl with the Dragon Tattoo, Dredd, Elysium, and Die Hard 4. Nmap was released to the public in 1997 and has earned the trust of millions of users.
As free software, we don't have any sort of advertising budget. So please spread the word that Nmap 7 is now available!
Top 7 Improvements in Nmap 7
Before we get into the detailed changes, here are the top 7 improvements in Nmap 7:- 1. Major Nmap Scripting Engine (NSE) Expansion
- As the Nmap core has matured, more and more new functionality is developed as part of our NSE subsystem instead. In fact, we've added 171 new scripts and 20 libraries since Nmap 6. Examples include firewall-bypass, supermicro-ipmi-conf, oracle-brute-stealth, and ssl-heartbleed. And NSE is now powerful enough that scripts can take on core functions such as host discovery (dns-ip6-arpa-scan), version scanning (ike-version, snmp-info, etc.), and RPC grinding (rpc-grind). There's even a proposal to implement port scanning in NSE. [More Details]
- 2. Mature IPv6 support
- IPv6 scanning improvements were a big item in the Nmap 6 release, but Nmap 7 outdoes them all with full IPv6 support for CIDR-style address ranges, Idle Scan, parallel reverse-DNS, and more NSE script coverage. [More Details]
- 3. Infrastructure Upgrades
- We may be an 18-year-old project, but that doesn't mean we'll stick with old, crumbling infrastructure! The Nmap Project continues to adopt the latest technologies to enhance the development process and serve a growing user base. For example, we converted all of Nmap.Org to SSL to reduce the risk of trojan binaries and reduce snooping in general. We've also been using the Git version control system as a larger part of our workflow and have an official Github mirror of the Nmap Subversion source repository and we encourage code submissions to be made as Github pull requests. We also created an official bug tracker which is also hosted on Github. Tracking bugs and enhancement requests this way has already reduced the number which fall through the cracks. [More Details]
- 4. Faster Scans
- Nmap has continually pushed the speed boundaries of synchronous network scanning for 18 years, and this release is no exception. New Nsock engines give a performance boost to Windows and BSD systems, target reordering prevents a nasty edge case on multihomed systems, and NSE tweaks lead to much faster -sV scans. [More Details]
- 5. SSL/TLS scanning solution of choice
- Transport Layer Security (TLS) and its predecessor, SSL, are the security underpinning of the web, so when big vulnerabilities like Heartbleed, POODLE, and FREAK come calling, Nmap answers with vulnerability detection NSE scripts. The ssl-enum-ciphers script has been entirely revamped to perform fast analysis of TLS deployment problems, and version scanning probes have been tweaked to quickly detect the newest TLS handshake versions. [More Details]
- 6. Ncat Enhanced
- We are excited and proud to announce that Ncat has been adopted by the Red Hat/Fedora family of distributions as the default package to provide the "netcat" and "nc" commands! This cooperation has resulted in a lot of squashed bugs and enhanced compatibility with Netcat's options. Also very exciting is the addition of an embedded Lua interpreter for creating simple, cross-platform daemons and traffic filters.
- 7. Extreme Portability
- Nmap is proudly cross-platform and runs on all sorts of esoteric and archaic systems. But our binary distributions have to be kept up-to-date with the latest popular operating systems. Nmap 7 runs cleanly on Windows 10 all the way back to Windows Vista. By popular request, we even built it to run on Windows XP, though we suggest those users upgrade their systems. Mac OS X is supported from 10.8 Mountain Lion through 10.11 El Capitan. Plus, we updated support for Solaris and AIX. And Linux users—you have it easy.
Press
Please mail Fyodor if you see (or write) reviews/articles on the Nmap 7 release. Here are the ones seen so far:Reasonably detailed (or with many comments) English articles:
- Reddit: Nmap 7 Released!
- Hacker News: Nmap 7 Release Notes
- The Register: New Wireshark, Nmap releases bring pre-Xmas cheer to infosec types
- Softpedia: After Wireshark 2.0, Nmap 7 Free Network Scanner Is Finally Here
- n0where.net: Network Exploration with Nmap: Nmap v7 Released.
- SecurityWeek: Nmap 7 Brings Faster Scans, Other Improvements
- SD Times: Nmap 7 is released
- Help Net Security: The top 7 improvements in Nmap 7
Permission is granted for journalists (or anyone writing about this Nmap release) to use any of the text or screen shots on this page. For quotes, you can email Fyodor atfyodor@nmap.org. Leave your phone number if you want a callback.
Screen Shots
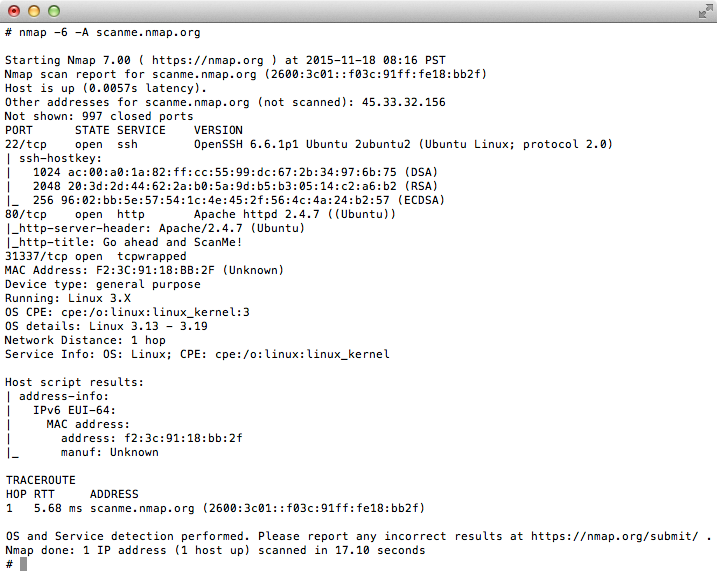
Nmap 7 provides a wealth of information about remote systems, as shown in this sample scan against a machine we maintain for scan testing purposes (scanme.nmap.org).

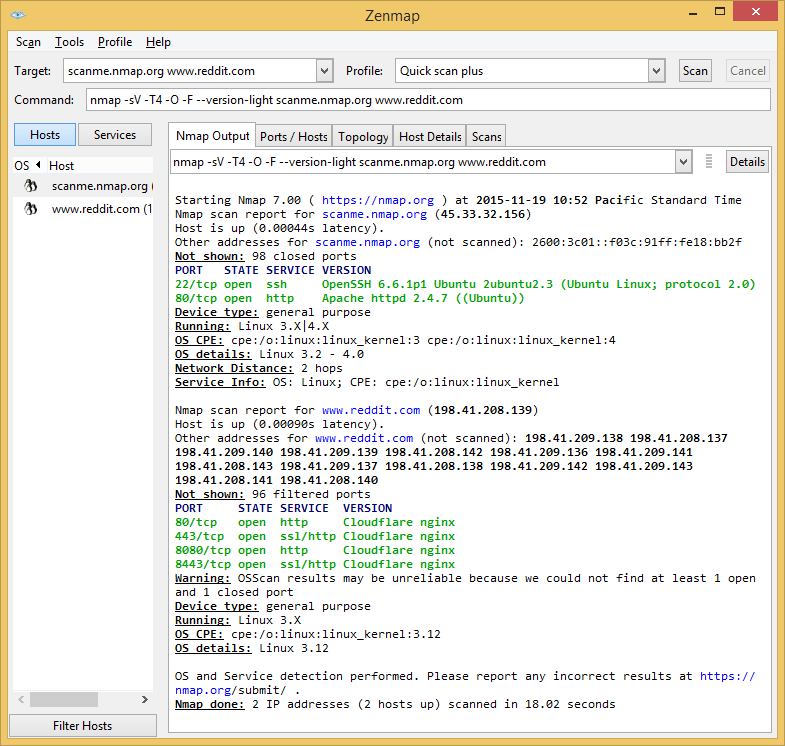
Here is an example using Zenmap on Windows 8.1 against a couple of production web servers (Nmap.org and Reddit).

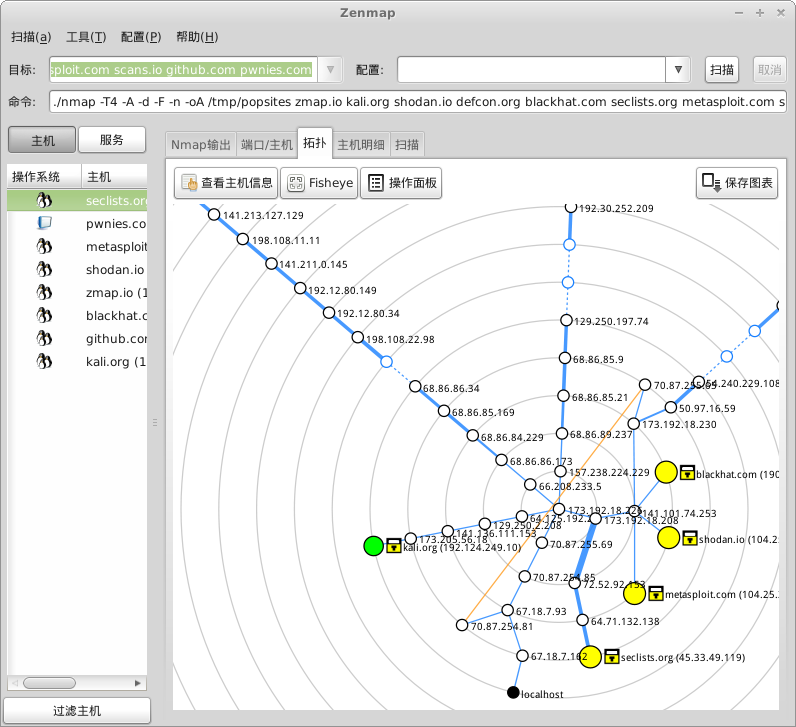
Perhaps the most visually appealing aspect of Zenmap is its network topology mapper. Here it is being used to interactively explore the routes between a source machine and a handful of interesting web sites, using the Chinese translation.

Detailed Improvements
The Nmap Changelog describes more than 330 significant improvements since our last major release (6.00 in May 2012). Here are the highlights:NSE Improvements
The Nmap Scripting Engine (NSE) is one of Nmap's most powerful and flexible features. It allows users to write (and share) simple Lua scripts to automate a wide variety of networking tasks. Those scripts are then executed in parallel with the speed and efficiency you expect from Nmap. The low learning curve and powerful networking libraries of NSE make it ideal for rapid development of security scanning and service probing scripts.- Script count has jumped from 348 to 515 scripts! That is 171 new scripts, minus four deletions. Of these, 109 will run by default when you use -sC, and another 35 will run with -sV for version detection. The list of new scripts is so long that we can't even include the summaries here, but each script is linked to it's own page on the NSE Documentation Portal for full details:
ajp-auth, ajp-brute, ajp-headers, ajp-methods, ajp-request, allseeingeye-info, bacnet-info, bjnp-discover, broadcast-ataoe-discover, broadcast-bjnp-discover, broadcast-eigrp-discovery, broadcast-igmp-discovery, broadcast-pim-discovery, broadcast-sonicwall-discover, broadcast-tellstick-discover, cassandra-brute, cassandra-info, cups-info, cups-queue-info, dict-info, distcc-cve2004-2687, dns-check-zone, dns-ip6-arpa-scan, dns-nsec3-enum, docker-version, enip-info, eppc-enum-processes, fcrdns, firewall-bypass,flume-master-info, freelancer-info, gkrellm-info, gpsd-info, hnap-info, hostmap-ip2hosts, hostmap-robtex, http-adobe-coldfusion-apsa1301, http-avaya-ipoffice-users, http-cisco-anyconnect, http-coldfusion-subzero, http-comments-displayer, http-cross-domain-policy, http-csrf, http-devframework, http-dlink-backdoor, http-dombased-xss, http-drupal-enum, http-drupal-enum-users, http-errors, http-exif-spider, http-feed, http-fetch, http-fileupload-exploiter, http-form-fuzzer, http-frontpage-login, http-git, http-gitweb-projects-enum, http-huawei-hg5xx-vuln, http-icloud-findmyiphone, http-icloud-sendmsg, http-iis-short-name-brute, http-ls, http-mobileversion-checker, http-ntlm-info, http-phpmyadmin-dir-traversal, http-phpself-xss, http-referer-checker, http-rfi-spider, http-robtex-shared-ns, http-server-header, http-shellshock, http-sitemap-generator, http-slowloris-check, http-slowloris, http-stored-xss, http-svn-enum, http-svn-info, http-tplink-dir-traversal, http-traceroute, http-useragent-tester, http-virustotal, http-vlcstreamer-ls,http-vuln-cve2006-3392, http-vuln-cve2010-0738, http-vuln-cve2013-0156, http-vuln-cve2013-7091, http-vuln-cve2014-2126, http-vuln-cve2014-2127, http-vuln-cve2014-2128, http-vuln-cve2014-2129, http-vuln-cve2014-8877, http-vuln-cve2015-1427, http-vuln-cve2015-1635, http-vuln-misfortune-cookie, http-vuln-wnr1000-creds, http-waf-fingerprint, http-webdav-scan, http-wordpress-users, http-xssed, icap-info, ike-version, ip-forwarding, ip-https-discover, ipv6-ra-flood, irc-sasl-brute, isns-info, jdwp-exec, jdwp-info, jdwp-inject, knx-gateway-discover, knx-gateway-info, llmnr-resolve, mcafee-epo-agent, metasploit-info, metasploit-msgrpc-brute, mikrotik-routeros-brute, mmouse-brute,mmouse-exec, mrinfo, msrpc-enum, ms-sql-dac, mtrace, murmur-version, mysql-dump-hashes, mysql-enum, mysql-query, mysql-vuln-cve2012-2122, nje-node-brute, omron-info, oracle-brute-stealth, pcanywhere-brute, qconn-exec, quake1-info, rdp-enum-encryption, rfc868-time, rmi-vuln-classloader, rpc-grind, s7-info, sip-call-spoof, sip-methods,smb-ls, smb-print-text, smb-vuln-conficker, smb-vuln-cve2009-3103, smb-vuln-ms06-025, smb-vuln-ms07-029, smb-vuln-ms08-067, smb-vuln-ms10-054, smb-vuln-ms10-061,smb-vuln-regsvc-dos, snmp-hh3c-logins, snmp-info, ssl-ccs-injection, ssl-date, ssl-dh-params, ssl-heartbleed, ssl-poodle, sstp-discover, supermicro-ipmi-conf, targets-ipv6-map4to6, targets-ipv6-wordlist, targets-xml, teamspeak2-version, tls-nextprotoneg, tor-consensus-checker, traceroute-geolocation, unittest, ventrilo-info, weblogic-t3-info,whois-domain, xmlrpc-methods - NSE became the tool of choice for rapid vulnerability scanning with the advent of celebrity vulnerabilities in 2014. NSE scripts have you covered for Heartbleed (ssl-heartbleed), Shellshock (http-shellshock), POODLE (ssl-poodle), Misfortune Cookie (http-vuln-misfortune-cookie), LOGJAM (ssl-dh-params), Stuxnet (smb-vuln-ms10-061), and even Slowloris (http-slowloris-check). Of course if you're also worried about less-celebrated vulnerabilities, the other 41 new "vuln"-category scripts should keep you busy.
- NSE joins the rest of Nmap in being able to output parseable XML. Instead of just a text blob in Nmap's XML output, scripts can now return structured information that can be quickly extracted with an XML parser. All new scripts produce structured output, most older scripts have been converted, and any script using the vulns library is automatically upgraded.
- The venerable RPC grinder which used to run with -sV is now an NSE script: rpc-grind. This allowed us to cull a bunch of old C code in favor of more maintainable Lua, as well as make a noticeable improvement in scanning speed, all while using a fifth of the number of code lines.
- HTTP and web scanning continued to dominate our NSE development. Over a third (57) of our new scripts were HTTP-related. Exceptionally exciting is the addition of NTLM authentication to the http library, which means http-brute can bruteforce Windows passwords, too. Script highlights include:
- http-slowloris exploits a resource exhaustion denial-of-service in Apache and similar webservers, based on the 6-year-old Slowloris attack script from RSnake.
- http-fetch acts a bit like a multi-target curl or wget, fetching the files you specify from every discovered webserver.
- http-server-header grabs the Server header from webservers and uses it to fill in service version information if -sV failed to find a match.
- http-webdav-scan detects WebDAV servers and grabs a directory listing.
- http-cross-domain-policy, http-csrf, http-dombased-xss, http-phpself-xss, and http-stored-xss check for various generic Web vulnerabilities. Similarly, http-errors checks for server-side bugs resulting in HTTP error codes.
- Oops, there was a vulnerability in one of our NSE scripts. If you ran the (fortunately non-default) http-domino-enum-passwords script with the (fortunately also non-default) domino-enum-passwords.idpath parameter against a malicious server, it could cause an arbitrarily named file to to be written to the client system. Thanks to Trustwave researcher Piotr Duszynski for discovering and reporting the problem. We've fixed that script, and also updated several other scripts to use a new stdnse.filename_escape function for extra safety. This broke our record of never having a vulnerability in the 16 years that Nmap has existed, but that's still a fairly good run!
- NSE libraries allow scripts to share code. In addition to the usual set of protocol helpers, some interesting additions include the LPeg parsing expression grammar library, a "ls" library for formatting directory listings, the "slaxml" XML parser, a pure-Lua Unicode library, and a unittest library currently used by 6 other libraries.
anyconnect, base32, bjnp, cassandra, eigrp, formulas, ike, isns, jdwp, lfs, lpeg, lpeg-utility, ls, ospf, rdp, re, slaxml, tls, unicode, unittest
Mature IPv6 Support
It came as no surprise when ARIN ran out of IPv4 addresses this year, and Nmap was already riding the wave to full IPv6 deployment. Nmap has supported IPv6 in some way since 2002, but improvements keep coming:- Idle scan is now supported with IPv6. IPv6 packets don't usually come with fragment identifiers like IPv4 packets do, so new techniques had to be developed to make idle scan possible. The implementation is by Mathias Morbitzer, who made it the subject of his master's thesis.
- Unicast CIDR-style IPv6 range scanning is now supported, so you can specify targets such as "en.wikipedia.org/120". Obviously it will take ages if you specify a huge space. For example, a /64 contains 18,446,744,073,709,551,616 addresses.
- In addition to ensuring IPv6 support in the majority of NSE scripts, Nmap 7 adds several IPv6-specific scripts for advanced host discovery and even denial-of-service:
- dns-ip6-arpa-scan performs a quick reverse-DNS lookup of an IPv6 network using a technique which analyzes DNS server response codes to dramatically reduce the number of queries needed to enumerate large networks.
- targets-ipv6-wordlist preys on the tendency of human network operators to use the enormous IPv6 address space and the hexadecimal alphabet to assign addresses that form words like "dead:beef". The wordlist is configurable, and the results are surprising!
- targets-ipv6-map4to6 similarly searches for manually configured addresses that correspond to a smaller range of IPv4 addresses that may be assigned to the same network.
- ipv6-ra-flood generates a flood of Router Advertisements (RA) with random source MAC addresses and IPv6 prefixes. Computers, which have stateless autoconfiguration enabled by default (every major OS), will start to compute IPv6 suffix and update their routing table to reflect the accepted announcement. This will cause 100% CPU usage on Windows and platforms, preventing to process other application requests.
- Nmap's parallel reverse-DNS resolver now handles IPv6 addresses. GSoC 2015 student Gioacchino Mazzurco rewrote the old C-style DNS code in beautiful C++ and a test suite, then fuzzed the living daylights out of it with afl. In addition to being very safe, this should result in faster -6 scans.
- IPv6 OS fingerprinting is improved, thanks to the efforts of Mathias Morbitzer and Alexandru Geana. Building on Mathias's research into new IPv6 OS fingerprinting methods, Alexandru spent the spring and summer of 2015 testing and adding features to our machine learning OS classifier. Using IPv6 guessed initial Hop Limit (analogous to IPv4's TTL) and the ratio of TCP initial window size to Maximum Segment Size (MSS), the classifier now matches with more confidence than ever. He also completed an extension of the classifier's training process to impute missing values from dropped or filtered packets, which lets Nmap make better guesses when network conditions are poor.
- Nmap's advanced traceroute is no longer limited to just using ICMP and TCP for tracing IPv6 hosts. The IPv6 --traceroute option is now equivalent to the IPv4 version and capable of using UDP, SCTP, and IPProto (Next Header) probes.
SSL/TLS scanning par excellence
SSL 3 deprecation, SHA-1 certificate deprecation, Heartbleed, CCS injection, POODLE, LOGJAM, FREAK, and RC4 deprecation—Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), have received a lot of attention in the past few years for security problems, and Nmap has emerged as the gold standard scanning tool for these issues.- One of our most popular NSE scripts is ssl-enum-ciphers, which enumerates SSL/TLS protocol versions (SSL 3 deprecation!) and ciphersuites (RC4 deprecation and weak export ciphers!). It has been enhanced beyond the old behavior of simply reporting "weak" or "strong" for each ciphersuite—it now scores each handshake using guidance from Qualys SSL Labs and taking into account server certificate strength, Diffie-Hellman parameter size, and encryption bit strength. It can safely scan the most finicky of SSL servers, safely negotiating long handshake intolerance issues and fragmented TLS messages. And it can run independently of version scan, since it is now capable of detecting TLS on unusual ports on its own.
- Detection of SSL and TLS by -sV has been boosted by including more popular TLS ports in the default lists and adding a new TLS-only service probe. Also, NSE scripts can now do TLS checks against LDAP, IMAP, and POP3 services which support STARTTLS (FTP, SMTP, and XMPP were already supported).
- At the core of our TLS NSE scripts is the new tls library, which enables quick development of robust scripts for checking vulnerabilities (ssl-heartbleed, ssl-poodle, ssl-ccs-injection, ssl-dh-params) or reporting configurations (tls-nextprotoneg, ssl-date).
Zenmap graphical front-end and results viewer

Zenmap is our cross-platform (Linux, Windows, Mac OS X, etc.) Nmap GUI and results viewer. It aims to provide advanced features for experienced Nmap users while also making Nmap easier for beginners to use. Frequently used scans can be saved as profiles to make them easy to run repeatedly. A command creator allows interactive creation of Nmap command lines. Scan results can be saved and viewed later, or even compared with one another to see how they differ. Our network topology viewer allows for interactive exploration of a network scanned with Nmap. Zenmap is now a mature tool, but it still got several enhancements since 6.00:
- Zenmap features a full translation capability for all menus, labels, buttons, and messages. Translations are available for 11 languages, including new Italian, Japanese, Polish, Chinese, and Hindi translations. The German and French translations were also updated.
- Support for large scans has drastically improved. We solved a CPU usage bug in opening large files and prevented the most common cause of out-of-memory problems by dropping the scrolling output window if it becomes a problem. Don't worry! The output is still saved to disk. Additionally, scans which have a lot of anonymous (unresponsive) traceroute hops will take up less space on the Topology page, since Zenmap will now assume hops at the same distance are the same device.
- Zenmap's display can filter hosts based on OS, ports, hostnames, and other criteria. Since 6.00 we also added negative matching, so you can exclude Windows systems for example with "os:!windows".
- Another sign of a maturing codebase, we've enabled unittest discovery in Zenmap, so running "make check" will run most of the existing Zenmap tests. Watch for more improvements in this area in upcoming versions!
Ncat
Ncat is a feature-packed networking utility which reads and writes data across networks from the command line. Ncat was written for the Nmap Project as a much-improved reimplementation of the venerable Netcat. It uses both TCP and UDP for communication and is designed to be a reliable back-end tool to instantly provide network connectivity to other applications and users. Ncat will not only work with IPv4 and IPv6 but provides the user with a virtually limitless number of potential uses.We are excited and proud to announce that Ncat has been adopted by the Red Hat/Fedora family of distributions as the default package to provide the "netcat" and "nc" commands! This cooperation has resulted in a lot of squashed bugs and enhanced compatibility with Netcat's options.
Some of the most exciting changes in Ncat 7 are:
- Ncat now features an embedded Lua interpreter! Similar to the Nmap Scripting Engine, the "--lua-exec" option makes it easy to write simple traffic filters and daemons in easy-to-learn Lua. A collection of example scripts, including a simple HTTP server, is included with the Ncat source.
- Ncat now supports Unix domain sockets (named pipes) on systems where those sockets are available. This is another Netcat compatibility enhancement, and it makes testing of Unix local services possible with Ncat.
- Ncat's proxy support was extended to support SOCKS5 with authentication.
- More compatibility corrections resulted in correct handling of EOF on all sockets, whether running as a client or as a server. The new --no-shutdown option keeps Ncat up and receiving network input after stdin is closed, just like traditional netcat's -d option.
Infrastructure Improvements
Keeping the Nmap project vibrant and productive (for developers and users) requires constant investment in our development. Improvements to Nmap's development and support infrastructure since Nmap 6 include:- The Nmap.org web site is now 100% HTTPS. This gives our users much-needed protection when downloading Nmap source and binary releases or submitting new service and OS fingerprints. Also, the GNU Mailman subscription pages for the Nmap-Announce, Nmap-Dev, and Full Disclosure mailing lists are hosted on Nmap.org and HTTPS-protected, so your subscription settings are safe, too.
- The Nmap Project has fully embraced Github Issues as its bug tracking solution. The Nmap-Dev mailing list is still going strong for discussion of Nmap development issues, but for user-submitted bug reports and enhancement requests, Github is the place to be. We also encourage code submissions to be made as Github pull requests. Even though the Github repo is still a read-only mirror of our authoritative Subversion repository, Github offers a great code review and discussion interface, as well as integrated code-quality-checking tools. As a convenience, issues.nmap.org is a redirector for issue numbers: http://issues.nmap.org/229 for example.
- On the subject of code quality, Nmap now integrates with Travis CI for continuous integration testing. If the build breaks, Nmap developers are notified immediately. Code contributions made as Github pull requests are automatically checked for build breakage, too. This is made possible by a concerted effort to enable "make check" to actually check and test Nmap code. So far, "make check" enables:
- Ncat test suite
- Nsock test suite
- Zenmap auto-discovered unit tests
- NSE tests through the unittest NSE script
- Ndiff tests
- Nmap's reverse-DNS engine test suite
- Nmap's changelog page is now displayed in linked and cross-referenced HTML, instead of as a simple dump of the CHANGELOG text file. URLs, issue numbers, script names, and NSE library names are all linked to the appropriate pages.
- SecWiki.org continues to be used by the Nmap development team for documentation and collaboration on long-term projects. Some popular pages are Nmap Code Standards,Nmap on Android, NSE Script Ideas, and the Nmap FAQ pages.
IPv4 Operating System Detection
Thanks to fingerprint submissions from thousands of Nmap users around the world, our remote operating system detection system grew from 3572 signatures in Nmap 6 to 4985 now. These include the latest versions of Windows, Linux, and Mac OS X as well as more specialized entries such as PLCs, lightbulbs, televisions, mainframes, and much more. Some of the newest fingerprints are for Apple iOS 9, Android 5.1, OpenBSD 5.7, FreeBSD 11.0, and a ton of new WAPs, switches, printers, and other devices.In addition to more than 1400 new fingerprints, we made several important performance improvements and bug fixes to the system. Most notably, if version detection determines a port to be "tcpwrapped," OS detection will prefer to use a different port for probing, since there's a good chance this is the result of a firewall interfering with TCP connections on that port.
Version Detection
The days when we could assume what was running on an open port based on the port number are long gone. These days, folks commonly run services on the "wrong" port numbers in order to defeat filtering policies, hide traffic, or work around various networking problems. Fortunately, Nmap's version detection system is able to interrogate the service listening on the open port and tell you the service running as well as (in many cases) the application name and version number. Nmap 6 had an impressive 8165 signatures matching 862 protocols, but Nmap 7 improves that to a whopping 10299 signatures for 1091 protocols!Additionally, Nmap 7 has 23 more service probes to pull information from remote services and more than double the number of softmatch lines (103), which help short-circuit the probing process to send the most-likely probes for the detected service.
Performance Improvements
In Nmap's 18-year history, performance has always been a top priority. Whether scanning one target or 20 million, users want scans to run as fast as possible without sacrificing accuracy. Improvements since Nmap 6 include:- For scans of targets that use different routes or interfaces, Nmap may now partially rearrange its target list for more efficient host groups. Previously, a single target with a different interface, or with an IP address the same as a that of a target already in the group, would cause the group to be broken off at whatever size it was. Now, we buffer a small number of such targets, and keep looking through the input for more targets to fill out the current group.
- Timeouts for many NSE scripts were reduced from tens of seconds to use a scaled timeout based on Nmap's portscan-phase timing determinations. A simple library function,stdnse.get_timeout, makes it easy for new script authors to do the same.
- Version scan is quicker now because of 56 more softmatch lines that prevent Nmap from sending irrelevant probes to certain services. Also, NSE scripts in the version categorynow obey the version intensity setting, so using an option like --version-light will prevent nearly all of these heavy-duty version probing scripts from running (unless you choose them by name).
- The old RPC Grinder, which used the original pos_scan engine from 1998, has been replaced by a much faster NSE script implementation. Scan times for version scanning (-sV) ought to improve greatly.
- New poll and kqueue Nsock engines allow for increased socket performance in Nsock-based scan phases (NSE and version scanning) on Windows, OS X, and BSD-derived systems that previously had to use the old select-based engine. Linux has had an epoll engine since Nmap 6.00.
Even More Improvements
In addition to the pages of changes listed above, we made many improvements which defy simple categorization:- The oft-requested --exclude-ports option has now been implemented! Easily avoid scanning off-limits or troublesome ports, without constructing complicated port ranges to avoid them. Safely integrates with -p, -F, and --top-ports.
- Nsock (and by extension Nmap's -sV and NSE) now supports connecting through chained proxies. Nmap adds the --proxies option to specify this proxy chain. While port scanning is not yet included, GSoC student and mentor Jacek Wielemborek has done groundbreaking work towards implementing TCP Connect scan in Nsock, so stay tuned!
- Instead of simply appending random data to Nmap scan packets with --data-length, try sending a message with the --data-string or --data options. Safely attribute your research or taunt your foes—it's up to you.
- Though in most cases ARP ping is the stealthiest, fastest, and most reliable host discovery method, you can now force the usual layer-3 discovery probes with the --disable-arp-ping option. This is useful in networks using proxy ARP, which make all addresses appear to be up using ARP scan. The previously recommended workaround for this situation, --send-ip, didn't work on Windows it is still missing raw socket support.
- For raw packet scans (i.e. not -sT), Nmap now reports the TTL of recieved packets in the Normal output if the --reason option is used. This was previously only available in the XML output, but is useful for detecting interfering firewalls in some cases. Additionally, --reason is enabled at verbosity 2 and higher.
- Fixed a bug which caused Nmap to be unable to have any runtime interaction when called from sudo or from a shell script on Linux. This was especially appreciated on Debian-based systems where Nmap is usually invoked with sudo.
- The beloved Nmap ASCII Dragon configure art now shares its spot with two other ASCII art pieces. Which one you get when you run ./configure is randomly chosen. Immediately below the art is a summary of what configure options were chosen, including a warning if OpenSSL could not be found and you didn't explicitly disable it.
- Nping now checks for a matching ICMP ID to avoid colliding with other running ping processes.
Moving Forward (Future Plans)
With this stable version out of the way, we are diving headfirst into the next development cycle. Many exciting features are in the queue, including:- A modern upgrade to the aging WinPcap is coming! We already have a working replacement called Npcap developed by GSoC student Yang Luo that is updated to use the NDIS 6 API and LWF. Cooperating with the WinPcap group, we can be sure that these improvements will be available in Nmap very soon.
- Nmap on mobile devices is already a reality for Android, but we want to expand support to other mobile platforms and perhaps develop a really useful app interface, since console applications tend to be difficult to use on those tiny screens.
- We are always working on improving performance, and you can expect we will deliver. Nmap's --min-rate option has the potential to scale to Internet-wide scans, and we intend to benchmark and demonstrate this ability. More large-scale scanning research should help us improve the port popularity rankings and fine-tune Nmap's internals for optimum performance.
- It doesn't take a Nostrodamus to predict that NSE will continue to expand at a blinding pace. We have dozens of NSE scripts waiting in the wings, and pages of ideas for new ones. Maybe your name will grace our CHANGELOG as a script author in the next release!
For the latest Insecure.Org and Nmap announcements, join the 117,175-member Nmap-hackers announcement list. Traffic rarely exceeds one message per month. Subscribe here orread the archives at SecLists.Org. To participate in Nmap development, join the (high traffic) nmap-dev list. You can also follow us on Twitter, Facebook, or Google+.
Acknowledgments
A free open source scanner as powerful as Nmap is only possible thanks to the help of hundreds of developers and other contributors. We would like to acknowledge and thank the many people who contributed ideas and/or code since Nmap 6.00. Special thanks go out to: Adam Saponara, Adam Števko, Aleksandar Nikolic, Alessandro Zanni,Alexandru Geana, Alexey Meshcheryakov, Alex Weber, Andreas Stieger, Andrew Farabee, Andrew Orr, Andrew Waters, Andrey Olkhin, Ange Gutek, Arturo Busleiman,Bill Parker, Brad Johnson, Brandon Paulsen, Brendan Coles, Chris Johnson, Chris Leick, Claudio Criscione, Claudiu Perta, Daniel Miller, Danila Poyarkov, David Fifield,David Matousek, Dhiru Kholia, Didier Stevens, Dillon Graham, Djalal Harouni, Dominik Schneider, Edward Napierała, Elon Natovich, Eric Davisson, Forrest B., Fyodor,George Chatzisofroniou, Gioacchino Mazzurco Giovanni Bechis, Greg Bailey, Gyanendra Mishra, Hani Benhabiles, hejianet, Henri Doreau, Jacek Wielemborek,Jan Reister, Jacob Gajek, jah, Jay Bosamiya, Jesper Kückelhahn, Jiayi Ye, Joachim Henke, John Bond, John Spencer, Jonathan Daugherty, jrchamp, Justin Cacak,Kurt Grutzmacher, Marek Lukaszuk, Marek Majkowski, Marin Maržić, Mariusz Ziulek, Mathias Morbitzer, Michael McTernan, Michael Meyer, Michael Schierl,Michael Toecker, Michael Wallner, Michal Hlavinka, Nicolle Neulist, Niklaus Schiess, nnposter, Olli Hauer, Patrick Donnelly, Patrik Karlsson, Paul AMAR,Paul Hemberger, Paulino Calderon, Pavel Kankovsky, Peter Malecka, Petr Stodulka, Philip Pickering, Pierluigi Vittori, Pierre Lalet, Piotr Olma, Pontus Andersson,Quentin Glidic, Raphael Hoegger, Raúl Fuentes, riemann, Rob Nicholls, Robin Wood, Ron Bowes, Sean Rivera, Simon John, Soldier of Fortran, Stephen Hilt,Tilik Ammon, Tom Sellers, Tomas Hozza, Tyler Wagner, Ulrik Haugen, Vasily Kulikov, and Vlatko Kosturjak.We would also like to thank the thousands of people who have submitted OS and service/version fingerprints, as well as everyone who has found and reported bugs or suggested features.
Special thanks go to Google, who has sponsored 73 students (total over the last 11 years) to spend a summer working on Nmap as part of Google's Summer of Code program. This summer, we had a team of five amazing students who contributed mightily to make Nmap even more powerful. We encourage you to read this year's project summary to learn more.

No comments :
Post a Comment